Introduction to Snyk
Snyk is a powerful security tool designed to identify vulnerabilities in code, infrastructure, and containers. It also scans open-source libraries to ensure comprehensive protection. Trusted by over 4 million developers, Snyk offers a faster and more efficient alternative to manual security checks while providing robust tracking capabilities.
Why to use Synk
At its foundation, Snyk operates on the principle that security should be accessible, actionable, and automated. The platform transforms complex security analysis into developer-friendly insights, enabling teams to maintain both velocity and security standards without compromising either objective.
Benefits and Use Cases
Risk Mitigation at Scale: Organizations adopting Snyk typically experience a 60-80% reduction in security vulnerabilities reaching production environments. This proactive approach prevents costly security incidents and reduces the technical debt associated with retroactive security fixes.
Developer Productivity Enhancement: By providing security feedback directly within development environments, Snyk eliminates the traditional friction between development velocity and security compliance. Developers receive immediate, actionable feedback without context switching between multiple tools or waiting for separate security team reviews.
Compliance Automation: Many regulatory frameworks, including SOC 2, ISO 27001, and industry-specific standards, require demonstrable security practices. Snyk's comprehensive reporting and audit trails provide the documentation necessary for compliance validation while automating many compliance-related processes.
Core Architecture and Philosophy
Snyk's architecture revolves around four interconnected security domains, each addressing specific vulnerability vectors in modern application development:
Source Code Analysis: Snyk Code employs static application security testing (SAST) techniques enhanced with artificial intelligence to examine proprietary source code. Unlike traditional SAST tools that often generate overwhelming numbers of false positives, Snyk Code focuses on providing high-confidence vulnerability detection with contextual remediation guidance.
Dependency Security Management: Snyk Open Source addresses the critical challenge of third-party component security. Given that modern applications typically comprise 70-90% open-source components, this capability becomes essential for maintaining application security posture.
Container Security Orchestration: Snyk Container extends security analysis into the containerized deployment layer, examining both base images and application containers for known vulnerabilities and misconfigurations. Infrastructure Configuration Validation: Snyk Infrastructure as Code (IaC) ensures that cloud infrastructure configurations follow security best practices before deployment, preventing misconfigurations that could lead to security incidents.
Integration Ecosystem The platform's strength lies in its extensive integration capabilities, supporting over 500 integrations across development tools, version control systems, continuous integration platforms, and deployment orchestrators. This comprehensive integration approach ensures that security analysis becomes a natural component of existing development processes rather than an additional burden.
1) Shift-left security 2) Automated vulnerability detection 3) Seamless CI/CD integration 4)License compliance
Technical Implementation Benefits
Shift-Left Security Strategy: Snyk enables organizations to implement true shift-left security practices by providing security analysis capabilities directly within integrated development environments (IDEs), pull request workflows, and continuous integration pipelines. This approach identifies and resolves security issues before they progress through the development lifecycle.
Intelligent Prioritization: The platform employs sophisticated risk scoring algorithms that consider multiple factors including exploitability, reachability analysis, and business context. This intelligent prioritization ensures that development teams focus their limited time on the most critical security issues rather than becoming overwhelmed by comprehensive vulnerability lists.
Automated Remediation Capabilities: Snyk goes beyond vulnerability identification by providing automated fix suggestions and, in many cases, automated pull requests containing the necessary code changes to resolve identified issues. This automation dramatically reduces the time and expertise required to address security vulnerabilities.
Organizational Use Cases
Enterprise Development Teams: Large organizations with multiple development teams benefit from Snyk's centralized policy management and reporting capabilities. Security teams can establish organization-wide security policies while allowing individual development teams to maintain autonomy in their implementation approaches.
DevOps and Platform Engineering: Organizations investing in DevOps transformation find Snyk particularly valuable for integrating security into their continuous delivery pipelines. The platform's API-first architecture and extensive automation capabilities align well with infrastructure-as-code and GitOps practices.
Regulatory Compliance Environments: Industries subject to strict regulatory requirements, such as financial services, healthcare, and government contractors, leverage Snyk's comprehensive audit capabilities and policy enforcement features to maintain compliance while supporting rapid development cycles.
Open Source Stewardship: Organizations that maintain or contribute to open-source projects use Snyk to ensure their contributions meet security standards and to monitor the security posture of their open-source dependencies.
Snyk Product Overview
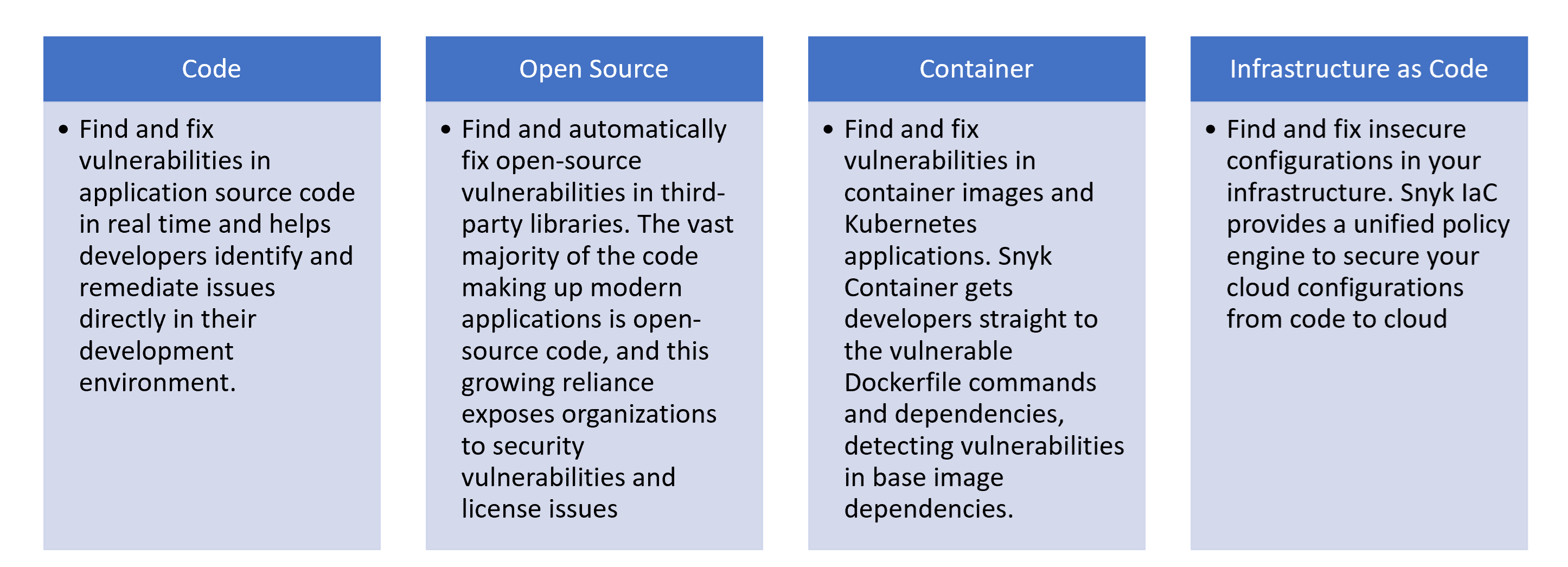
Platform Integration
Snyk's developer security platform takes a developer-first approach to security and integrates with leading IDE, repository, CI/CD, runtime, registry, and issue management tools. The platform is designed to integrate seamlessly into the Software Development Life Cycle (SDLC) to help developers identify and fix security issues early in the development process. These four components work together to provide comprehensive security coverage across the entire application development and deployment pipeline, from source code to cloud infrastructure.
Getting Started
Create Snyk Account and Single Command to install via npm - npm install -g snyk. Post that developer can connect to repositories and registries
Scanning with Snyk
Commands snyk test snyk monitor snyk auth
and these are used in Use in CI/CD pipelines
CLI Deep Dive
Policies and Reporting
Set severity thresholds Enforce license policies
Most popular Licenses
1) Eclipse Public License 1.0 (EPL-1.0): A weak copyleft license maintained by the Eclipse Foundation. It allows users to modify and distribute the software but requires that modifications be made available under the same license.
2) Eclipse Public License 2.0 (EPL-2.0): An updated version of EPL-1.0, offering better compatibility with other open-source licenses. It allows projects to dual-license under GPL-compatible terms and clarifies patent rights.
3) GNU Lesser General Public License v2.1 (LGPL-2.1): A free software license that allows developers to use and integrate LGPL-licensed components into proprietary software while ensuring modifications to the LGPL-covered components remain open-source
4) MIT License: A highly permissive open-source license that allows software to be reused with minimal restrictions. Users can modify, distribute, and use the software freely, as long as they include the original license and attribution.
5) Apache License 2.0: Similar to the MIT License but with added protections for patent rights. This ensures contributors grant users a license to use their patents related to the project while also requiring modifications to be clearly documented.
6) GPL (General Public License) Family: A set of copyleft licenses (such as GPLv2 and GPLv3) that require any derivative works to also be open-source and distributed under the same license. This ensures that software remains free for all users.
7) BSD Licenses: A family of permissive licenses (such as the 2-Clause and 3-Clause BSD Licenses) that allow software to be used, modified, and redistributed with fewer restrictions. Unlike GPL, BSD-licensed projects do not require derivative works to remain open-source.
8) MPL (Mozilla Public License): A hybrid license that is more permissive than GPL but still requires modifications to licensed files to be made public. It allows mixed proprietary and open-source components, making it suitable for commercial and community-driven projects.
9) AGPL (Affero General Public License): A strong copyleft license similar to GPL, but it extends requirements to software used over a network. This means that even web applications built on AGPL-licensed software must provide source code to users.
10) Non-SPDX Licenses: These include non-standard or custom licenses that are not part of the SPDX (Software Package Data Exchange) list but are still supported in various open-source projects. They may have unique conditions or modifications based on specific use cases.
Many organizations have application developed internally and being used internally or externally. here is chart that shows violations and guidelines to fix them.
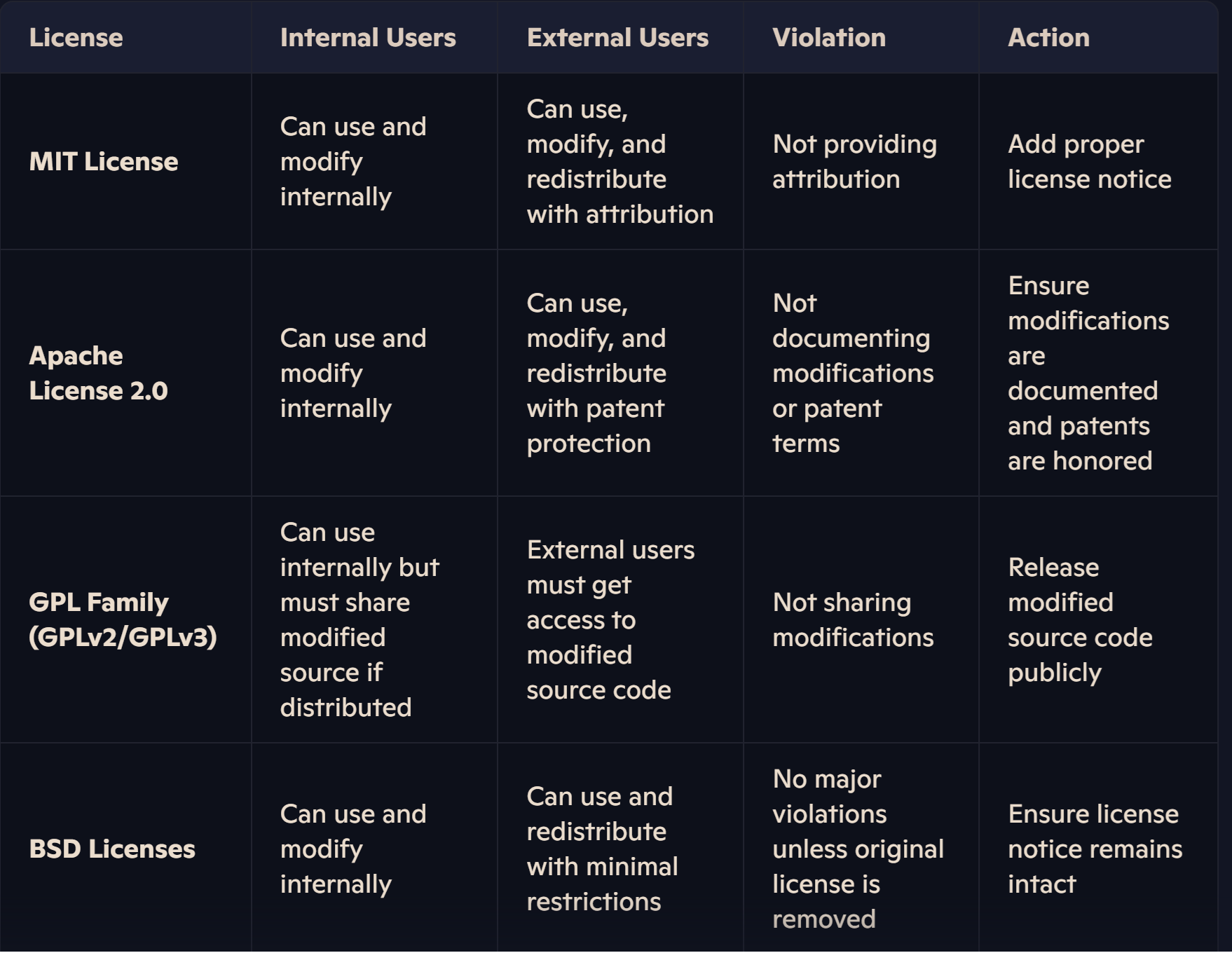
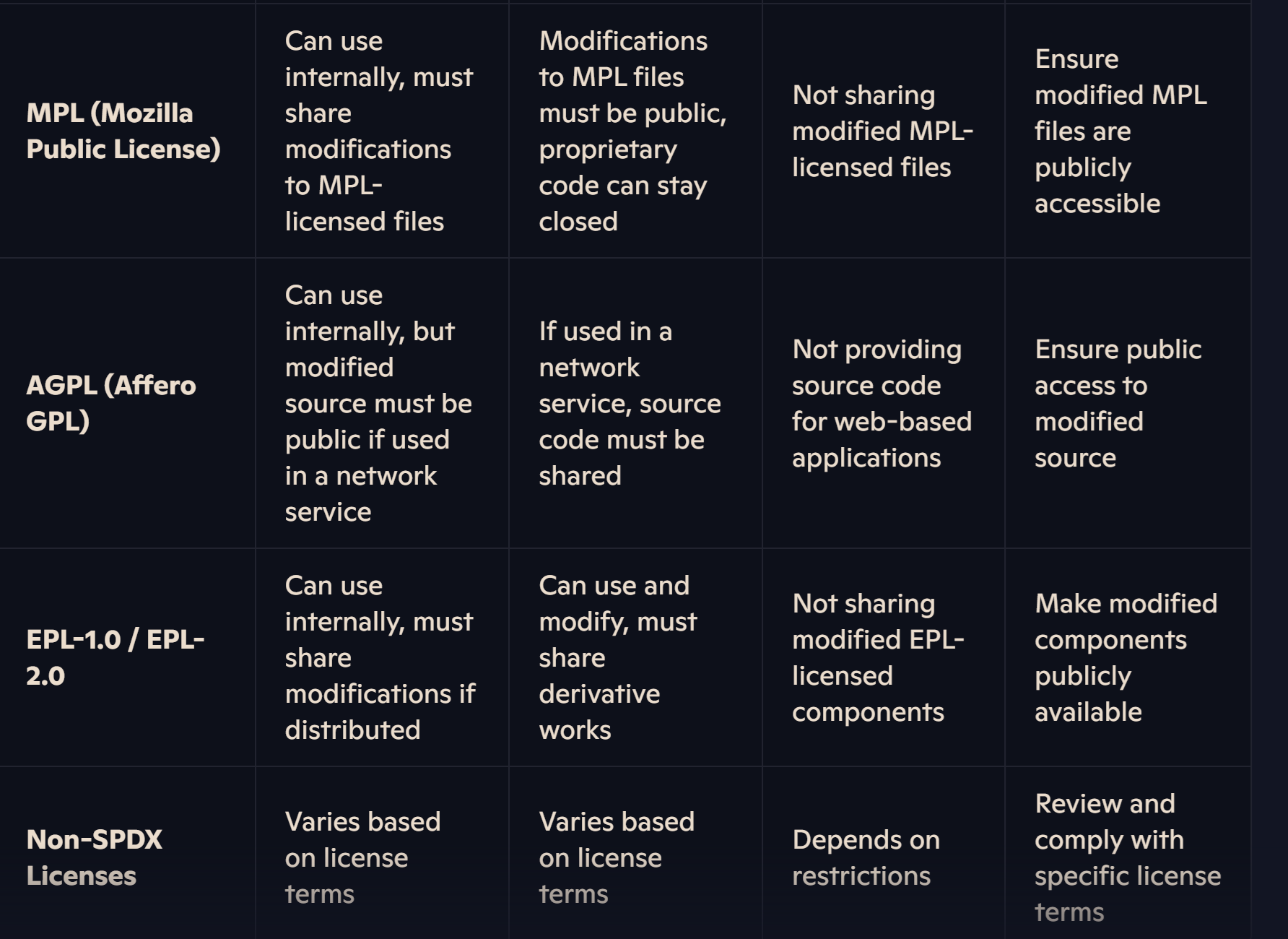
Ignore rules and expiry
Best Practices
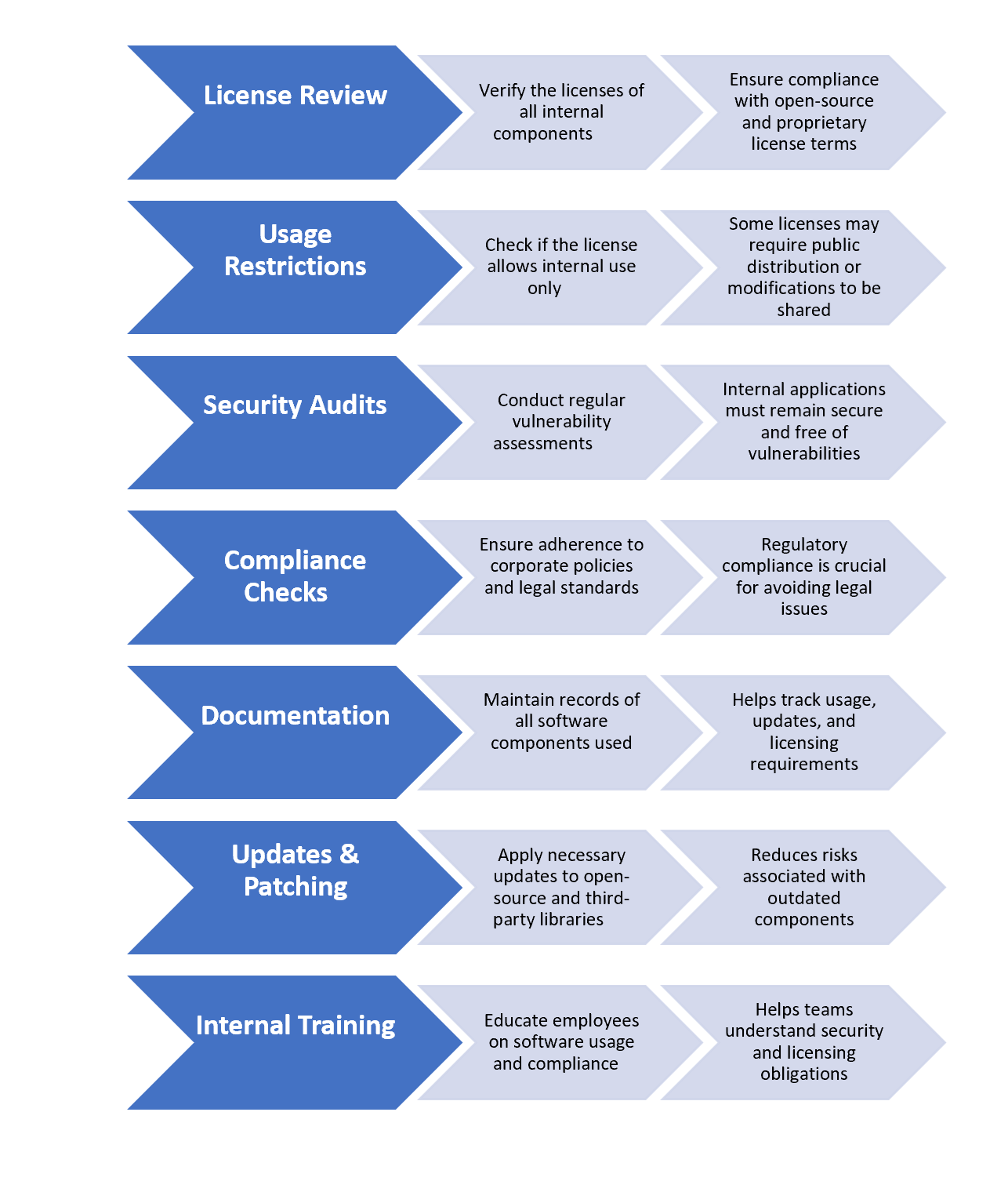
Educate developers on security findings
Hands-on Labs